Security Information and Event Management (SIEM)
Centralise all security logs from cloud, hybrid, and on-premises environments for rapid, prioritised threat investigation

What is SIEM? The Foundation of Security Monitoring
Security Information & Event Management (SIEM) is a cyber security solution which collects and analyses log and event data across your entire IT environment.
Whether you require foundational threat monitoring, extended log retention, or advanced threat protection, we tailor our SIEM solutions to fit your IT security strategy.

Key Functions of SIEM
According to the NIST Cybersecurity Framework, continuous monitoring is a critical component of modern security operations. SIEM platforms enable this monitoring by unifying security data into actionable insights. This monitoring extends across cloud, on-premises, endpoints, and networks, detecting threats in real time while ensuring compliance. It’s core functions include:
-
Collects and centralises log and event data from all IT systems
-
Detects anomalies and potential threats in real-time
-
Generates alerts for suspicious activity
-
Provides compliance reporting for regulations such as GDPR, ISO 27001, and PCI DSS
At Red Helix, we help businesses determine the right SIEM strategy based on their specific needs. Whether you need enterprise-wide log analytics and compliance monitoring with Sumo Logic or advanced endpoint threat detection with CrowdStrike, our team ensures seamless integration and expert management. Investing in the right SIEM solution improves security efficiency, reduces operational costs, and enhances overall resilience against evolving cyber threats.
Not sure which SIEM fits your organisation best? We’ll help you make an informed decision based on your infrastructure, security needs, and compliance requirements.
Contact us today for a consultationHow SIEM helps Organisations
Effective security information and event management (SIEM) is vital for every business, allowing them to improve their security posture and deliver on key business objectives.
But managing a SIEM tool can be resource heavy, leading to many businesses struggling to keep up with the skills needed to make the right decisions.
This is where our managed security monitoring service, with tailored support options, can take away the pain and let you concentrate on what matters most, your customers.

Managed SIEM for Small and Medium Sized Businesses
For SMBs, opting for a managed SIEM is a great option. SIEM enables SMBs to streamline threat detection, incident response, and compliance management processes via a unified log management system. This ensures complete visibility into their networks with maximum ease of use. Often smaller and medium sized businesses do not have the resources or budget to spend on employing and managing an in-house Security Operations Centre (SOC). A managed SIEM therefore provides a cost-effective, scalable solution and enhances capabilities without requiring an in-house security team. Managed SIEM bridges the gap, providing enterprise grade protection at an affordable cost.
Benefits of SIEM
SIEM | Traditional Security Services (Log Management, IDP/IPS) |
|---|---|
| Aggregates data from various security tools, network devices, applications, and operating systems | Focuses on specific data sources like network traffic (IDS/IPS) or system logs (Log Management) |
| Correlates events from various sources to identify security incidents | Analyses individual data sources for suspicious activity |
| Generates prioritised alerts based on security rules and threat intelligence | Generates alerts based on pre-defined rules |
| Provides comprehensive reports on security incidents, trends, and user activity | Offers limited reporting capabilities specific to the data source |
| Manages large volumes of data from diverse sources | Limited customisation options |
The Power of Cloud SIEM
Using the cloud for SIEM offers many benefits over on-premise solutions:
Cloud-based SIEM can scale with your business needs, handling growing data volumes without requiring costly in person, hardware upgrades.
Unlike on-prem solutions that require manual updates, cloud SIEM providers ensure your system is always running the latest security patches and features.
Cloud SIEM eliminates the need for significant upfront investments in infrastructure.
With cloud SIEM, security teams can monitor, analyse, and respond to threats from anywhere, making it ideal for remote work environments and global operations.
Leading cloud providers offer high availability, disaster recovery, and encryption, ensuring resilience against cyber threats and minimising business downtime.

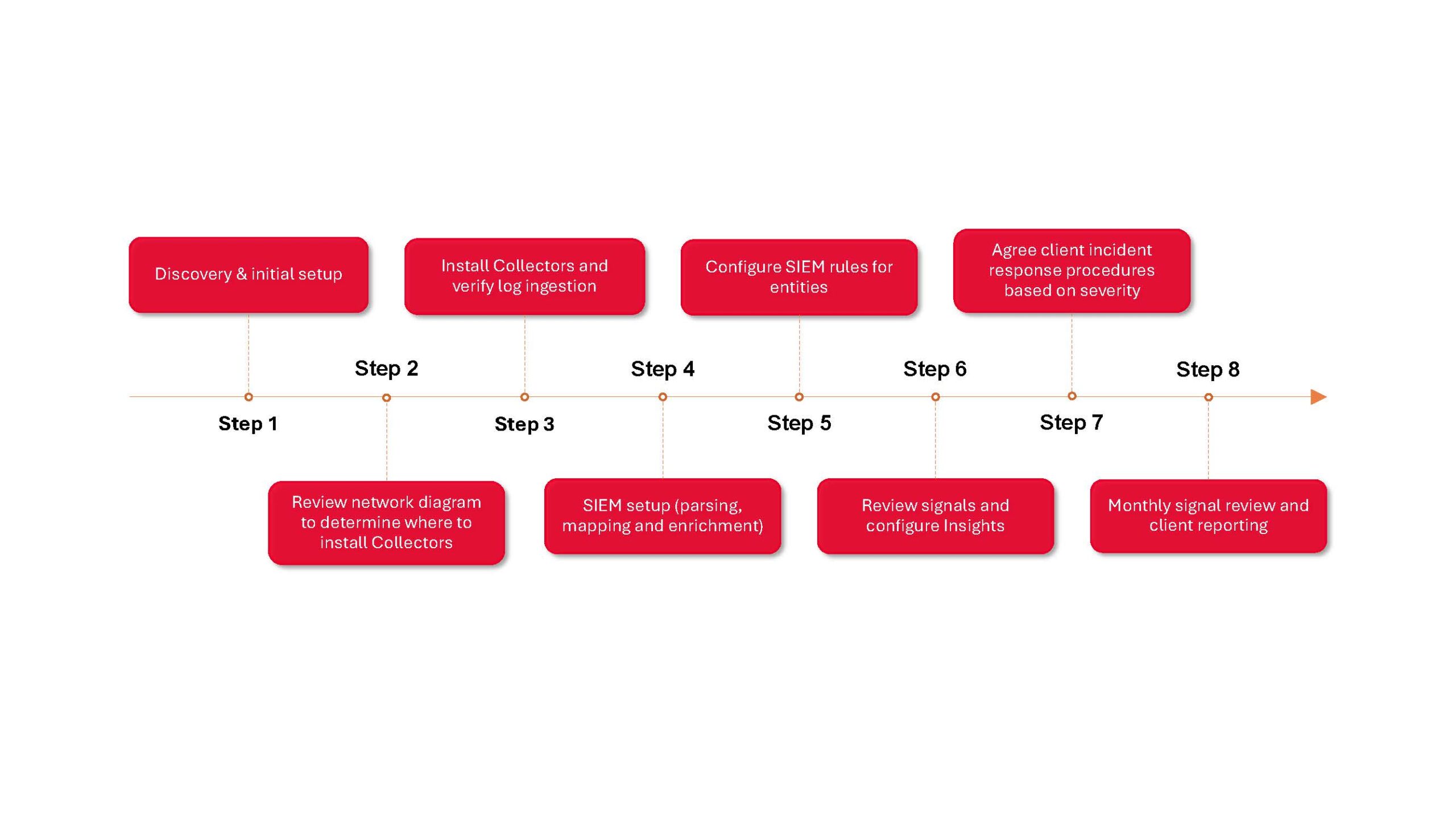
Managed SIEM services
We combine the best SIEM technology with people-centric persistence to deliver key business outcomes, tailored to your organisation.
- Review and prioritisation of actionable insights, investigating details to determine the type and severity of a threat to determine the action that needs to be taken.
- Management of rules to ensure your SIEM system setup is tailored to your organisation.
- Incident response tailored to your organisation.
- Daily checks to review log ingestion, signal generation and actionable insights, ensuring your SIEM instance is configured and functioning correctly.
- Weekly in-depth reviews and fine tuning of your SIEM instance to improve your security posture.
- Monthly usage to appraise how logs are being ingested, ensuring the most efficient use of your instance.
- A monthly summarised report comprising of data volume, signal categories, actionable insights, and incidents seen in the previous month with advice where applicable to pre-empt potential areas of compromise or attacks, and any new feature or enhancement that has been made available during that period.

How to integrate a SIEM with other tools
At Red Helix, we offer a Managed Detection and Response service which combines Endpoint Detection and Response, Network Detection and Response, as well as Security Information and Event Management. Outsourcing these tools combined allows you to gain comprehensive visibility across your IT environment. Our SOC team works 24/7 to provide detection and response capabilities for you.
Choosing the right SIEM provider can make or break your organisation’s cyber security strategy. With so many options available, it’s critical to find a partner that offers real-time threat monitoring, seamless integration with your IT stack, compliance expertise, and 24/7 support. You should consider the key factors to ensure your SIEM solution delivers maximum protection and operational efficiency.
How to choose your Managed SIEM providerService attribute | Supported | Managed |
|---|---|---|
| SIEM instance setup |  |  |
| Log ingestion setup |  |  |
| Rule configuration |  |  |
| Actionable insight setup |  |  |
| Dashboard setup |  |  |
| Alert configuration |  |  |
| SIEM support |  |  |
| Monthly checks |  | |
| Reports |  | |
| Threat investigation |  | |
| Rule management |  | |
| Daily and weekly checks |  | |
| Incident response |  |
How we evaluate the SIEM technology that underpins our service
Our Managed SIEM platform is continuously tested and improved to meet evolving cyber security, compliance, and visibility demands. If you’re managing SIEM internally or with a UK Managed Security Services Provider, make sure these essential elements are built into your approach.
FAQs
Traditional SIEM is becoming outdated as companies move towards the cloud as legacy logging systems are becoming redundant in the complex cyber security landscape. The current situation with SIEM technology is comparably lacking, however modern improvements are on their way.
This can be overcome by implementing into your network alongside other security solutions such as EDR and NDR.
Managed SOC capabilities handle and respond to incidents, whereas managed SIEM focuses on data collection, analysis, and threat detection.
No, a firewall allows or denies traffic in or out of a network, whilst a SIEM analyses the network data collected via log files.
Yes, SIEM uses security logs to alert for potential breaches, and then employs its analytical technology and event correlation to determine true infections and potential origin points of the malware.
No it cannot. XDR offers organisations new security capabilities and enhanced protection, it cannot and should not fully replace SIEM. This is because SIEM capabilities go further than XDR by employing log management, compliance and threat data analysis and management. An XDR solution can be helpful for organisation’s security posture, however it needs to be integrated alongside a SIEM to fulfil all needs.
Yes, a managed SIEM integrates with cloud environments, EDR, NDR, firewalls, and identity tools for unified security.