Network Detection & Response (NDR)
Protect your business with hybrid network detection, response and security compliance.

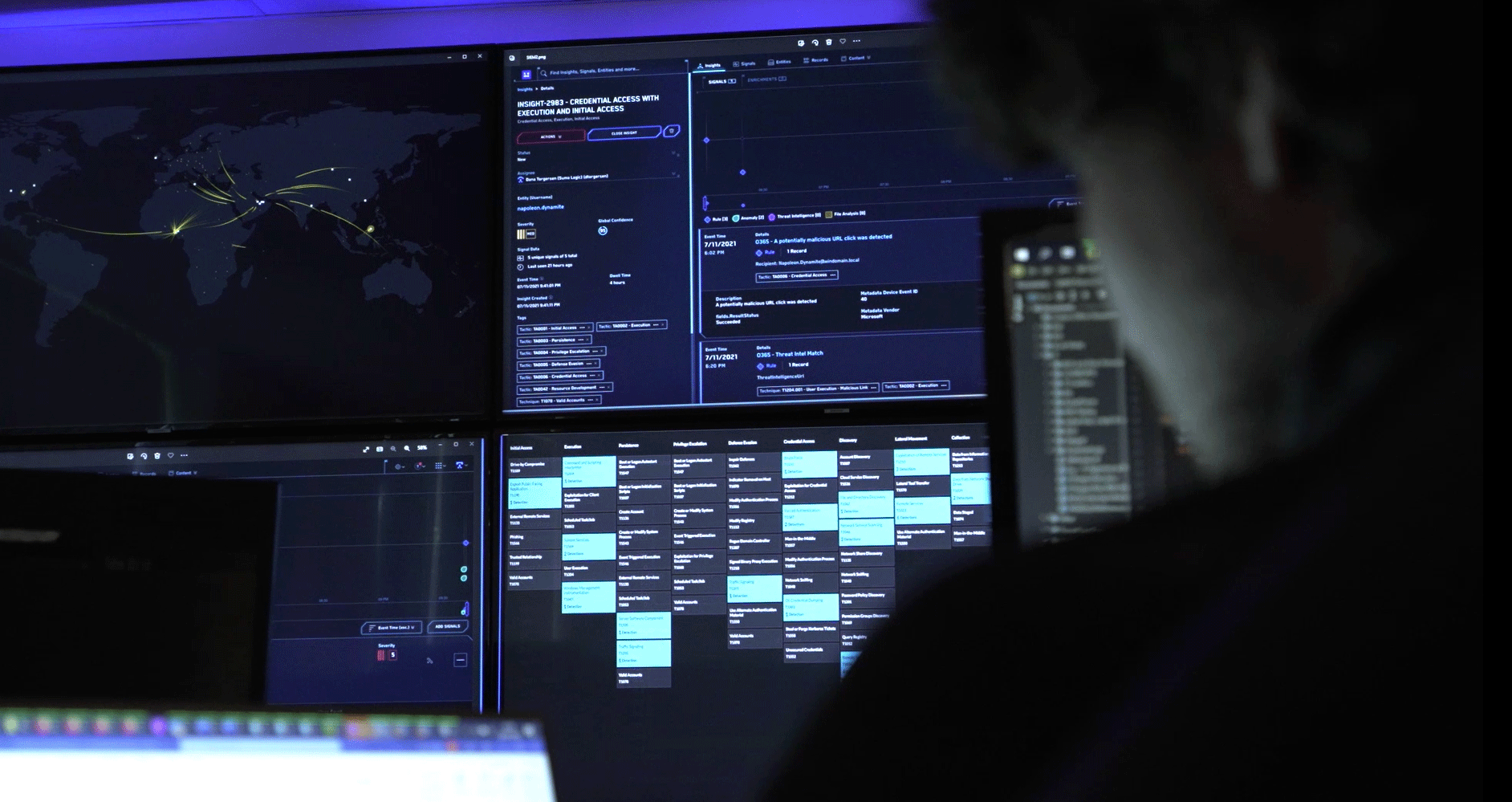
Network Detection and Response (NDR) is a technology solution which uses artificial intelligence, machine learning and behavioural analytics to monitor network traffics. This provides a baseline of activity which can be used to track any malicious or anomalous activity and identify potential threats. This continuous analysis evolves with the network, ensuring that it is always up to date.
What does Network Detection & Response (NDR) do?
Previously, Network Traffic Analysis (NTA) was the established method of monitoring company’s networks, however, as cyber-criminals became more advanced, there came a need for a more innovative solution. NDR technology builds on the capabilities of NTA by adding behavioural analysis and threat response. Gartner renamed the solution ‘NDR’ in 2020 as a more relevant description of what NDR does.
The type of cybersecurity risks NDR searches for include unknown malware, targeted attacks, insider attacks, and risky behaviour.
Why do you need Network Detection & Response (NDR)?
Traditional threat detection security tools operate by looking for unique Indicators of Compromise (IoCs) and signatures. They can identify these from the line of code, file hash, or size of the malware variant. This information is updated in databases and means that threats can be detected by scanning for the presence of these signatures in network traffic.
However, this is very limiting. These tools cannot detect new or unknown malware or threats because they can only identify threats that they already know. They are detection-focused, which is no longer effective against modern cyber security threats. In contrast, NDR solutions are dynamic, so they can actively hunt for threats. This makes them essential to maintaining a healthy network security. Even when a threat is unknown, NDR technology can identify it and alert the security team, so protecting the entire network. NDR solutions provide incident response automation and security tools, alerting SOC teams to potential malicious activity and running automated responses to optimise threat investigations and minimise impact. Overall, these systems ensure increased visibility across the network.
NDR provides security teams with broad attack visibility and knowledge of potential threats, which means that false negatives are largely avoided. As well as this, it provides additional analytical data, which lead to increased accuracy in threat detection. By using technology such as behavioural analytics and AI, NDR provides more precise and accurate threat hunting, as well as out-of-the-box detection.
NDR is more efficient than alternative solutions. Cyber threats are detected early on, and mitigated before damage can be done to the network. Cloud-delivered analytics has increased access for remote workers which has grown in importance for our current cyber landscape.
| Identifies which assets on your network are not protected |  |
| Uses AI and Machine Learning |  |
| Captures and analyses IoT device traffic |  |
| Detects Man-in-the-middle attacks |  |
| Continually monitors network traffic |  |
The SOC visibility triad
Having an NDR solution complements the ‘SOC visibility triad’ (Network Detection and Response (NDR), Endpoint Detection and Response (EDR), and Security Information and Event Management (SIEM)) which ensures a completely protected security portfolio as security teams are provided with all the necessary tools to hunt threats.

NDR from Red Helix
Our service complements our Endpoint Detection & Response (EDR) service, supporting your IT team by protecting your infrastructure from cyber-attacks, ransomware, and internal threats.
We provide comprehensive network detection, response, and compliance across your network infrastructure, protecting you from attacks that can bypass Anti-Virus and EDR solutions, which rely heavily on signature and threat intelligence updates to be effective. Full network visibility requires both NDR and EDR.
NDR leverages innovative artificial intelligence (AI) and machine learning (ML) technology and a cloud-native architecture, taking NetFlow for traffic analytics with log data from cloud providers, Active Directory logs, as well as application events from Office365 and G-Suite, correlating them against a variety of AI models to achieve maximum coverage. Using AI/ML, NDR can detect threats and associate them down to devices and user accounts. Our service reduces high volume network traffic into prioritised alerts, remediation activities, and threat & compliance reports.
NDR monitors the network continuously giving you network visibility across your infrastructure, providing a real-time asset inventory, able to detect abnormal network activity, rogue and unprotected devices, threats to IoT devices, unprotected ports, with compliance reporting covering NIST, Cyber Essentials, FFIEC, NIAC, CMMC, and more.
Get in touch| Network Detection & Response (NDR) tools |
|---|
| AI & Machine Learning analytics |
| Deep Packet Inspection |
| Threat intelligence integration |
| Network Traffic Analysis |
| Automated incident response |
| Deception technology & Honeypots |
| Cloud & IoT security monitoring |
Our NDR managed service supports your IT team by protecting your hybrid infrastructure from cyber attacks, ransomware and internal threats.
Stop attacks
We detect and stop cyber threats that target your infrastructure. We’ll also monitor your VPNs, directories and cloud platforms and respond when needed. Our service can be deployed quickly and easily to keep pace with your growing infrastructure.
Identify threats
Breaches don’t just come from cyber criminals. Accidental or malicious internal actions can be just as damaging. We analyse networks to look for anomalous activity, unsanctioned devices, missed software patches, unprotected ports, and other things that can leave you vulnerable to attack.
Show compliance
Let us track SLAs and show your Cyber Essentials adherence. We can also tailor reports as and when you need them. Need to demonstrate compliance with international standards like NIST and CMCC? We’ve got you covered.
Watch our NDR overview
Network Detection & Response (NDR) best practices
1.Establish your Network visibility
You should assess your network infrastructure to identify blind spots or areas which lack visibility. This evaluation should cover cloud, on-prem, and remote environments to ensure it is thorough. Visibility into encrypted traffic, lateral movement, and shadow IT is essential for early threat detection.
2.Implement baseline monitoring
Monitor and analyse network traffic patterns over a period to establish a baseline of normal network behaviour. This will serve as a reference point to indicate whether there are any anomalies or potential threats. This baseline should be regularly updated changes occur in the environment.
3.Tailor detection rules
Customise your NDR solution’s capabilities to align with specific organisation security requirements. This fine tuning should be based upon your industry, network architecture, and the current threat landscape.
4.Incorporate with existing security infrastructure
Integration with existing security tools and infrastructure e.g., SIEM, firewalls, and EDR platforms is necessary. This streamlines the response process and ensures comprehensive visibility across your network. For example, integrating NDR with SIEM platforms enables automated threat containment, such as isolating compromised devices and blocking malicious traffic.
5.Continuous monitoring
Your NDR solution should operate in real-time, continuously monitoring and analysing network traffic. This quick response is critical in remediation capabilities and ensuring minimal impact.
6.Staff training
Your security team should be trained in effectively using your NDR solution to leverage its full potential.
7.Automate incident response
Leverage automation and orchestration capabilities to improve the efficiency and effectiveness of your NDR deployment. Automate repetitive tasks, such as log analysis and alert triaging, to reduce manual effort and response time.
By following these NDR best practices, organisations can enhance their security posture, improve threat detection and response capabilities, and effectively leverage their NDR investment to protect their critical assets and sensitive data. This ensures that your solution can be utilised to its optimal ability.
Contact us to discuss your needs and explore how we can tailor our managed NDR service to your requirements

Support
Whether you want us to provide and set up your NDR solution or manage it for you on a day-to day-basis, we have your needs covered.
This service is ideal for organisations that want to manage their own NDR solution, but with the confidence that they have a team of experts available to help with the setup and ongoing support. Working with you, we will:
Help to set up your NDR solution, including:
- Initial setup
- Integrations
- Security zones
- Objectives and goals
- Policies
- Alerting
- Dashboards
- Compliance reports
- Service and security reports
- Provide ongoing NDR support.
Everything you get with Supported as a Managed Service, plus:
- Review and prioritisation of actionable insights, investigating details to determine the type and severity of a threat to determine the action that needs to be taken.
- Management of policies to ensure your NDR solution setup is tailored to your organisation.
- Incident response tailored to your organisation.
- Daily checks to ensure your NDR instance is configured and functioning correctly.
- Weekly in-depth reviews and fine tuning of your NDR instance to improve your security posture.