Cyber Maturity Review
A structured, independent review that benchmarks maturity, exposes blind spots and provides a practical path to measurable improvement.
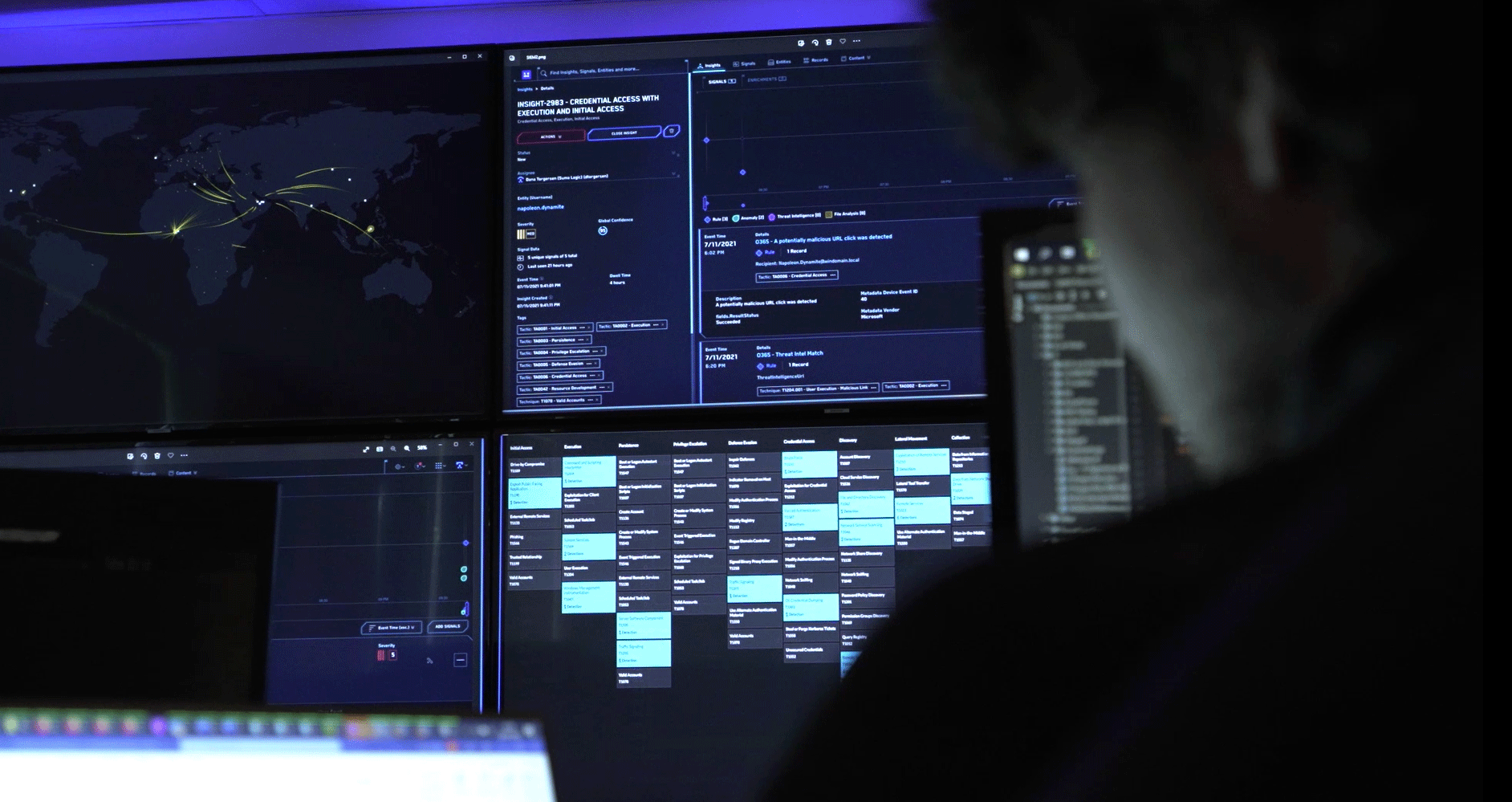
A Cyber Maturity Review delivers a calm, evidence-led view of where your security programme stands today and what is required to strengthen it. It gives technology, risk and business leaders a single, accurate understanding of capability across people, process and technology.
Mapped to recognised frameworks such as CAF and NIST, the review replaces fragmented insight with a coherent baseline. It enables organisations to move from assumption to certainty, ensuring investment and effort are guided by risk rather than activity or noise.

Why cyber maturity matters
Security decisions become difficult when visibility is incomplete. Security teams may be working hard but still exposed. Controls may exist but operate inconsistently. Compliance actions may consume time without reducing real risk.
A cyber maturity review establishes a clear foundation. It highlights where controls are effective, where gaps exist and where duplication or misalignment is creating unnecessary effort. Most importantly, it helps organisations prioritise what matters most and build resilience with confidence.

A practical view of maturity
Red Helix brings engineering precision together with pragmatic, human guidance. Every review is delivered by specialists who understand how environments operate in practice, not how they appear in documentation.
We combine technical assessment, objective governance evaluation and practical risk insight to produce a maturity view that stands up to scrutiny. This approach is strengthened by integrated expertise across penetration testing, risk assessment, governance design, assurance and security behaviour. The result is a broad but coherent perspective that supports organisations at every stage of maturity.
What the Cyber Maturity Review covers
Structured assessment of governance, technology, controls, behaviour and operations aligned to CAF and NIST functions.
Clear prioritisation that reflects real-world likelihood, business impact and existing control effectiveness.
Focused analysis of vulnerabilities, misconfigurations and architectural weaknesses across on-premises, cloud and hybrid environments.
Evaluation of monitoring, detection, response and recovery capabilities, including incident response readiness.
Independent review of policy completeness, ownership, roles and decision-making structures.
Targeted offensive testing to validate assumptions, identify weaknesses and inform maturity conclusions.
Practical validation of identity controls, endpoint protection, cloud posture, email security and backup integrity.
Mapping against statutory, regulatory and industry expectations, highlighting evidence gaps and achievable improvements.
Clear, non-technical outputs for executives, including maturity heatmaps, gap summaries and investment options.
A phased plan that shows what to remediate, improve and optimise to reach your target maturity.
 | Seeking an independent view of current cyber capability |
 | A leader needing clarity before investing in new tools or restructuring security |
 | Recovering from incidents and looking to stabilise and strengthen posture |
 | A team wanting measurable improvement and a roadmap you can own |






